Wireless Security Protocols Ppt Powerpoint Presentation Infographic Template Sample Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

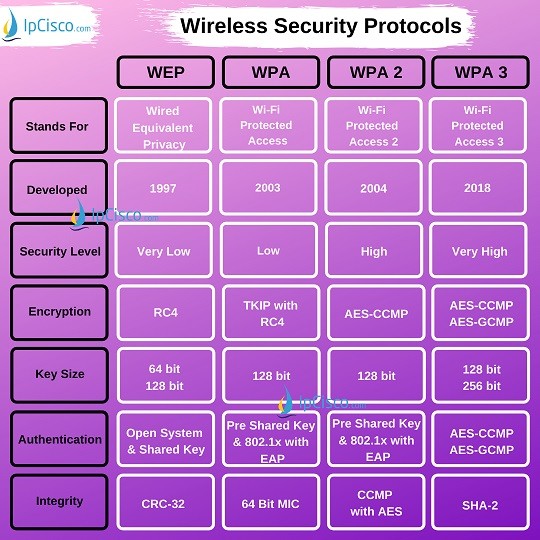
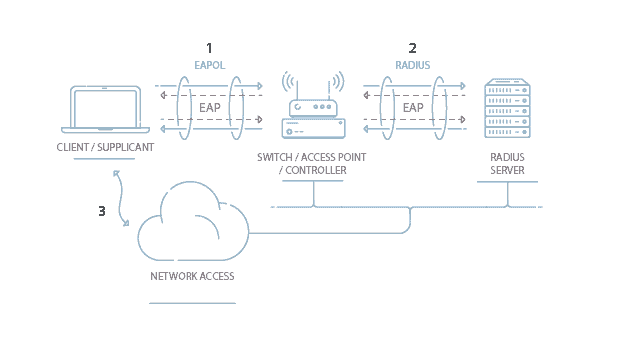
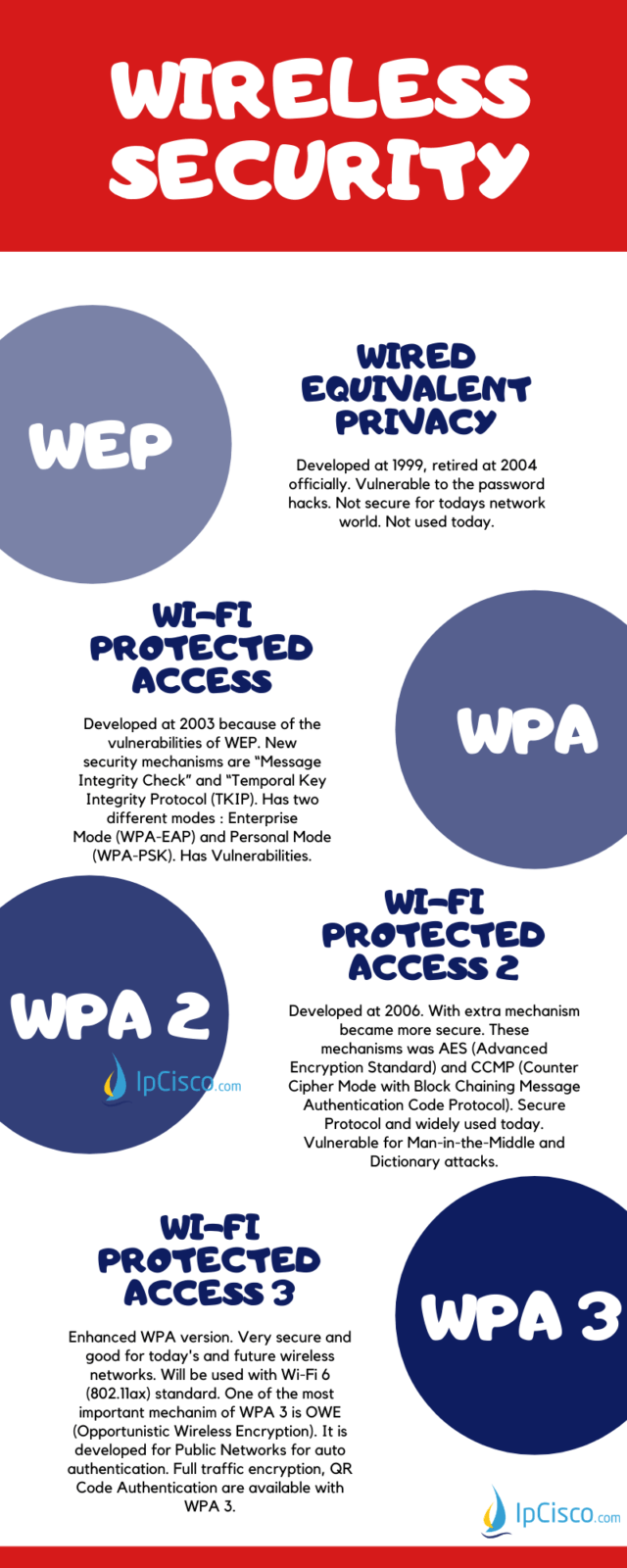
This wireless security protocol allows 192-bit minimum-strength security protocols and cryptographic tools to protect sensitive data, such as GCMP-256, HMAC-SHA284, and ECDSA using a 384-bit elliptic curve. Which is the wireless security